Jeoss WIFI Sniffer
Many times when setting-up a server it results extremely handy being able to sniff network traffic on the server's interfaces. We will show here how to use a capture daemon able to remotely transmit the captured traffic to a GUI Wireshark. The ultimate challenge would be capturing raw unauthenticated WIFI traffic.
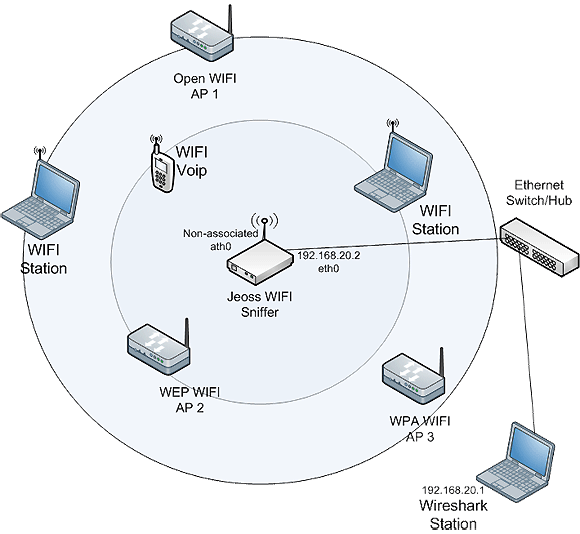
Then, the idea is to set up a Jeoss box able to capture WIFI traffic and retransmit it on an Ethernet connection to a remote Wireshark station.
a) On our Jeoss Box
Let's consider our Jeos box has one or two Atheros interfaces and one or more Ethernet interfaces.
Let's start with /etc/network/interfaces looking something like this:
# The loopback network interface
auto lo
iface lo inet loopback
# The ethernet network interface
auto eth0
iface eth0 inet dhcp
auto eth0:0
iface eth0:0 inet static
address 192.168.20.2
netmask 255.255.255.0
broadcast 192.168.20.255
gateway 192.168.20.1
Let's stop our Atheros WIFI card/s
patrick@jeoss804:~$ sudo airmon-ng stop ath1
patrick@jeoss804:~$ sudo airmon-ng stop ath0
Let's start ath0 listening in monitor mode on all channels
patrick@jeoss804:~$ sudo airmon-ng start wifi0
Depending on our box configuration we can get an answer like this:
patrick@jeoss804:~$ sudo airmon-ng start wifi0
Found 1 processes that could cause trouble.
If airodump-ng, aireplay-ng or airtun-ng stops working after
a short period of time, you may want (some of) them!
PID Name
3931 dhclient3
Interface Chipset Driver
wifi0 Atheros madwifi-ng
wifi1 Atheros madwifi-ng
ath0 Atheros madwifi-ng VAP (parent: wifi0) (monitor mode enabled)
Then we kill the potentially problematic process related to ath0
patrick@jeoss804:~$ sudo kill 3931
Now we can inspect the whole WIFI spectrum and decide which channel we are going to analyze deeper.
patrick@jeoss804:~$ sudo airodump-ng ath0
CH 10 ][ Elapsed: 8 s ][ 2010-09-13 08:08 BSSID PWR Bea #D, #/s CH MB ENC CIPHER AUTH ESSID 00:60:B3:F3:F0:66 22 30 13 0 7 54e. WEP WEP WLAN_78 00:25:68:EE:EB:20 18 18 0 0 1 54e WPA CCMP PSK vodaEB1F 00:03:C9:8C:F9:34 17 14 0 0 11 54 OPN Comtrend 00:1A:2B:00:75:9A 16 20 0 0 3 54 WEP WEP WLAN_FA 00:26:F2:5F:6E:8E 16 19 0 0 6 54e WPA2 CCMP PSK HIPOCRATES 00:22:15:75:7E:4E 9 10 0 0 1 54 WEP WEP Karlos 00:26:5A:9A:31:86 9 11 0 0 6 54e. WPA2 TKIP PSK f.tower 00:1A:2B:2B:4A:00 9 10 0 0 11 54 WEP WEP JAZZTEL_30 00:1A:2B:5D:D8:F1 7 6 0 0 11 54 WEP WEP JAZZTEL_DC 00:1A:2B:6F:7B:32 6 10 0 0 3 54 WEP WEP WLAN_22 00:24:D1:16:60:75 5 6 0 0 11 54 WPA TKIP PSK x11 00:11:F5:49:1D:2F 4 3 0 0 11 54 WPA TKIP PSK xmon_df 00:24:D2:23:7B:61 3 4 0 0 5 54e WEP WEP Smith2010 BSSID STATION PWR Rate Lost Packets Probes 00:60:B3:F3:F0:66 00:13:E8:76:33:8D 48 0 - 1 22 3 WLAN_78 00:23:08:E3:B1:86 00:23:4D:5F:12:41 4 0 - 1 0 7 00:1A:2B:2B:4A:00 00:23:32:37:29:AA 14 0 -11 0 2 (not associated) 00:16:CF:AD:2A:E5 2 0 - 1 0 2 WLAN_DD
We decide to analyze the traffic on channel 7, then we stop and start ath0 but this time telling it to listen in monitor mode only on channel 7
patrick@jeoss804:~$ sudo airmon-ng stop ath0
patrick@jeoss804:~$ sudo airmon-ng start wifi0 7
Let's start our packet capture daemon with the Jeoss box Ethernet interface (eth0) IP 192.168.20.2 as the Wireshark communication interface.
patrick@jeoss804:~$ sudo rpcapd -b 192.168.20.2 -n
Rpcapd 1.1.1 for Debian/Ubuntu/Jeoss by Patrick Masotta (2010)
www.vercot.com\~jeoss\
Press CTRL + C to stop the server...
b) On our Windows/Linux PC running Wireshark (this how-to uses Windows Wireshark v1.4.0)
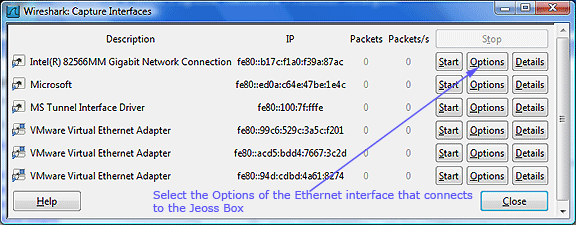
Menu Capture/Interfaces...
select the "Options" of the Ethernet Interface that connects to the Jeoss Box
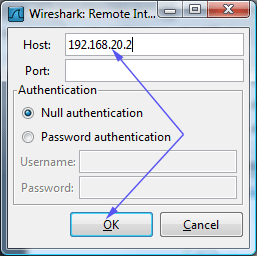
Select Interface Remote...
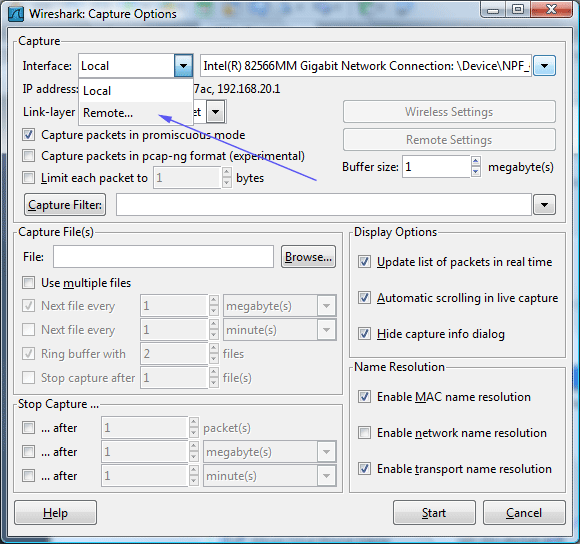
Type Jeoss Box Ethernet IP address
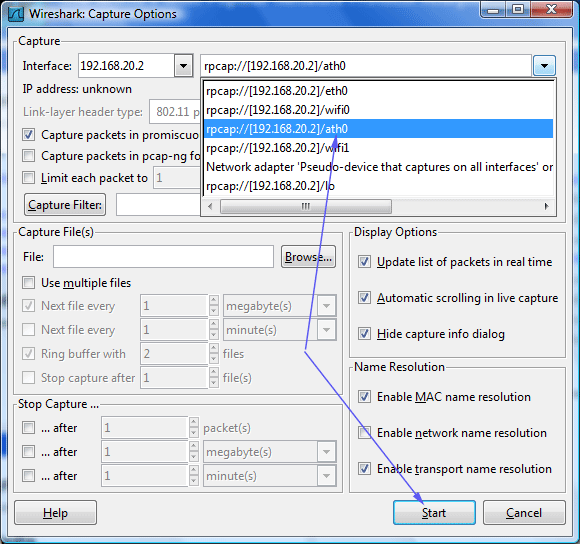
Select the remote capture interface rpcap:/[192.168.20.2]/ath0 and Start capturing
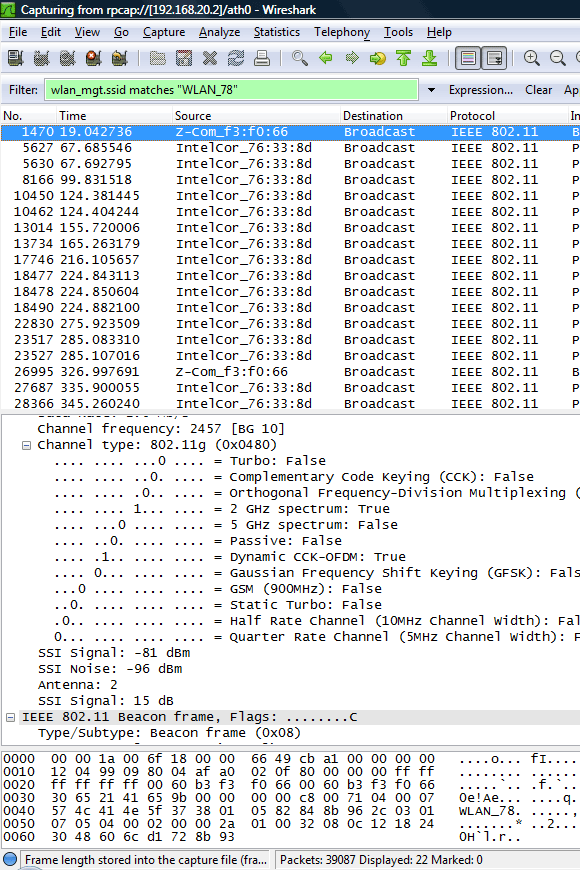
Next picture shows a capture of "real" 802.11 traffic where we filter packets that match ssid=WLAN_78
NOTE1: This set-up requires a Jeoss install + the included optional collections "Madwifi-ng" and "Rpcapd"
NOTE2: rpcapd is a good tool for troubleshooting our server traffic but using it on a production server could lead to a security breach when a remote un-authenticated computer can receive the traffic of our server ports.